Background
As a regular reader of this blog, you already know I use a dual-boot setup on my laptop where Ubuntu 22.04 is installed alongside Windows 11.
Yesterday,14th August, I had to work on my Windows machine and before turning it off, I saw that there were updates available. And I think I’m not the only one here who is notoriously weak to those yellow/orange dots on the Windows shutdown/restart/sleep menu options, and I can’t resist clicking on them and updating Windows.
So, what I did, I just hit “Update and shut down”, business as usual xD. However, this time, it was unfortunately not business as usual. The installed update (August 13, 2024—KB5041585 (OS Builds 22621.4037 and 22631.4037)) just corrupted something which I don’t exactly what, but it seems it’s related to Secure boot. The update corrupted the shim SBAT, which stands for Secure Hardware Information Management Secure Boot and Attestation Tool. It’s a security mechanism used in modern computing systems, particularly in Windows, to ensure the integrity of the boot process and verify that only trusted software is loaded during system startup.
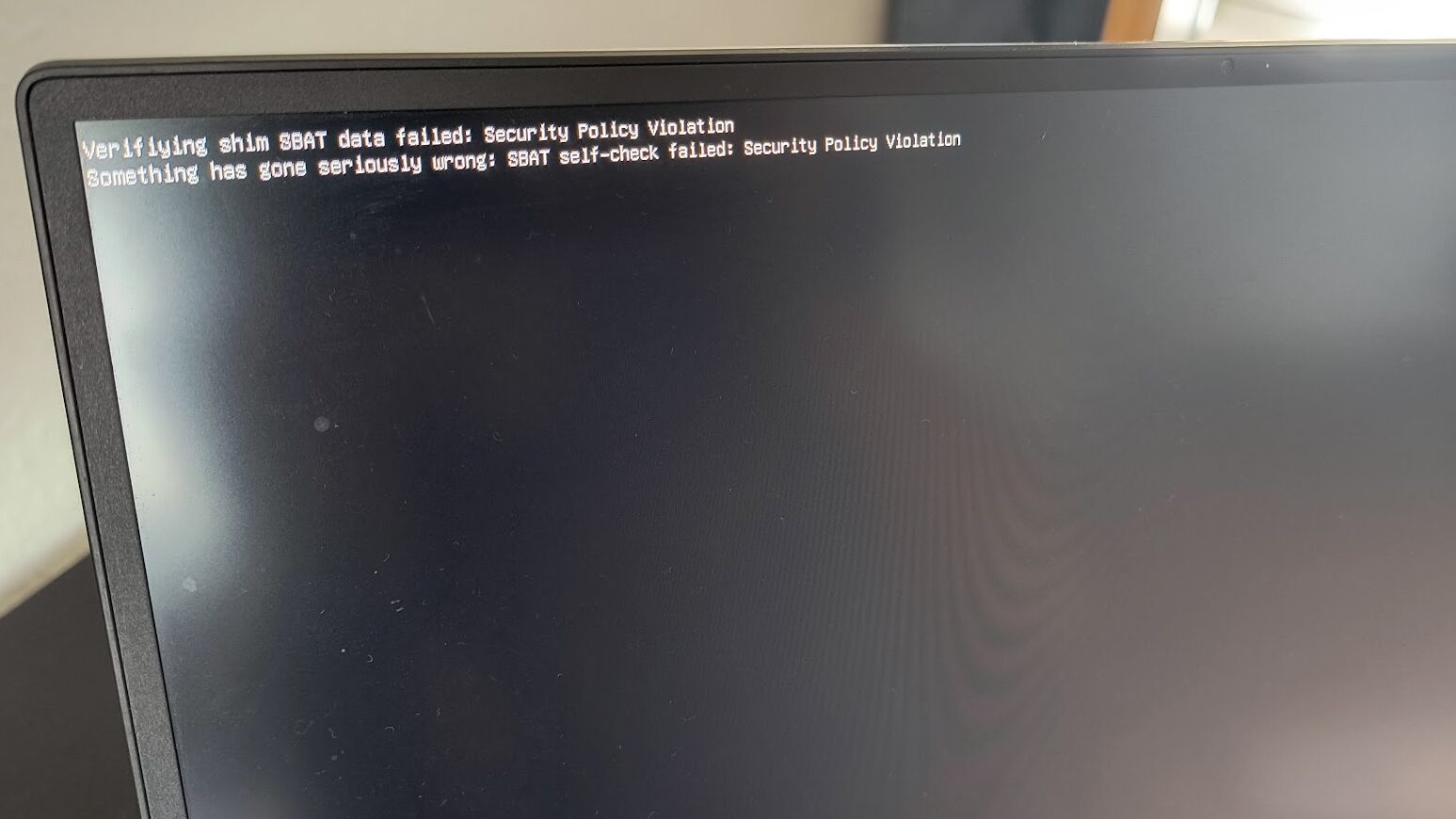
What happened, I was not able to boot into Ubuntu any more, and after the machine booted up, I got the following message:
Verifying shim SBAT data failed: Security Policy Violation. Something has gone seriously wrong: SBAT self-check failed: Security Policy Violation.
Solution
After spending hours on the internet searching for a solution, I found the solution to this problem.
- Disable Secure Boot in your UEFI settings. In my case (Dell XPS), I had to press F2 during booting and then navigate to Secure Boot –> disable secure boot. Restart, now you must be able to log in to your Ubuntu.
- Open the Ubuntu terminal (CTRL+SHIFT+T) and execute the following command:
mokutil --list-sbat-revocationsthe output will be similar to the following:sbat,1,2024010900 shim,2 grub,3 - If yes, run the following command
sudo mokutil -set-sbat-policy delete - Reboot Ubuntu, and again run the command from 2, you are supposed to see
sbat,1,2021030218 - If yes, reboot again, and via the UEFI settings screen enable secure boot. You will be able to use dual-boot as you have always been doing 🙂
But wait what the heck is mokutil ? It’s a tool to import or delete the machine’s owner keys (MOK) stored in the database of shim. You can read more about this tool using this link
Leave a Reply